Stegosaurus?
I've got one more for you here:
Obscurity
You've managed to get yourself into some of the internal emails passing around the system and it turns out this new guy is pretty on point security-wise. After learning of the horrendous state of their admin management he's begun a crusade to get it sorted. There's good news and bad news, good news is you no longer need to pick apart that data snippet for a password, bad news is they changed it and have been applying security changes to the network that could make your life pretty difficult. Some additional good news is you realized you might be about to lose access and with a push your team has managed to secure the file attached which is as far as you can tell the password database you've been seeking, problem is they've done something to it. While your team were on there they heard the password had been changed and searched for the new one, they didn't find it but were able to liberate its hash. It's one of these two, we don't know what the other one is for but it must be something related given the context, so let's get cracking!
e5e9fa1ba31ecd1ae84f75caaa474f3a663f05f4
9a2bed63580555b66d12451dd96146f2d27daae0503a0c92f3fc2e737b486edd
So obviously this puzzle picks up from the last, and as you've probably guessed from the name it goes deeper into warning you of the dangers of security by obscurity and how little protection it actually gives you. Unlike the last one though this puzzle has 15 flags. Yes, all in that one file, I'll include a full list of all 15 at the end to check against. As before feel free to give this one a go, see how far you can get unaided, and then follow along with this walkthrough, you never know you might learn something. If you're curious the fastest solve was 1 day 15 hours and 14 minutes from puzzle release to last valid flag received, I'm pretty confident it can be done much faster if given all your attention so by all means, run the gauntlet and see how well you do!
Alright so this one starts out a lot easier, if you aren't familiar with a .7z file its basically just a zip using a OS agnostic tool called 7zip. Shouldn't take much to extract it and then you'll be presented with... a jpeg? Checking again you'll see nothing else, just an image of the Horus Heresy, yes nerds are common in the tech industry, so what do we do with that?

Well, this image isn't exactly what it appears, you may not know but images can be used to hide information with a technique known as Steganography hence this week's title, all you need are the right tools to unpick it. One of the most commonly used tools for this sort of trick is known as Steghide, you can have a read all about how to use their tool on their website. Once you've got it installed fire it up to test the image and see what we can find out.
~> steghide info HorusHeresy.jpg "HorusHeresy.jpg": format: jpeg capacity: 39.5 KB Try to get information about embedded data ? (y/n) y Enter passphrase:
Hello there, passphrase? I think we now know what those hashes are for. If you don't know hashes they can be used for all sorts of things, checksums and verifications, and more importantly here they are often used for storing passwords. Now if you don't know much about password hashing so far I recommend starting with Tom Scott on Computerphile and also watch the follow up video How NOT to Store Passwords where he very accurately points out all the big mistakes people have and still make with storing passwords. Hopefully you've now got a basic knowledge of hashing and can avoid making the mistake we're about to exploit.
We could make a start with something like hashcat or rainbowcrack, but we don't need to, for simple stuff like this we don't need any of those fancy tools, instead open Google. Type "hash crack online", hit Enter, there you go, dozens of sites where we can just do this online. Using CrackStation putting both hashes in it tells me we have 2 different kind of hashes, which makes sense since they have different lengths as usually hashes will have a specific length they are supposed to be.
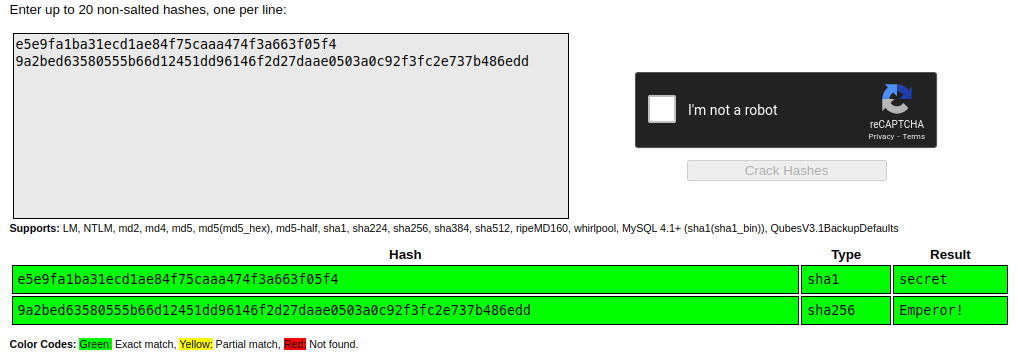
So it looks like we have a SHA1 hash that is secret and a SHA256 hash that is Emperor!. Given that the second one has a direct link to the image you might try that one first, if you do you'll have no luck which is probably a good thing as people could just guess the passphrase. The first password though, simple as it is, renders an interesting response.
~> steghide info HorusHeresy.jpg
"HorusHeresy.jpg":
format: jpeg
capacity: 39.5 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "data.tar":
size: 20.0 KB
encrypted: rijndael-128, cbc
compressed: yes
So there's a tar file (short for tape archive which is what was used in backups that the compression was typically used for) embedded within the image, so we best dig it out then. You should be able to find the syntax to extract it listed in the Steghide documentation.
~> steghide extract -sf HorusHeresy.jpg Enter passphrase: wrote extracted data to "data.tar".
The tar file simply wants extracting which is nice and easy, Google will tell you the command you need if you don't already know. Upon doing so inside you'll find a pair of files, some sort of corrupted image and a text file, name Nota Bene, which is something you normally see written on musical staff notation. It's Italian, and means "note well" or "please note", sounds like its got some useful info, so lets have a read.
This broken image is not what it appears, it is the database you have been looking for but we've modified it slightly for security. Be sure to use this note as a key. We have also taken the liberty of obscuring each of the passwords while we revamp our security. Everything you need is in the notes, we've also changed the password to it, if you get stuck just contact the admin team!
Sounds like its a note for their staff, it also contains the first flag, nice! So the information sounds kind of cryptic at first glance, the image is a database? Use the note as a key? To understand what this all means its time we did a bit of research. What we've been searching for is a password database, you may remember from the previous puzzle it was a Keepass database, so probably time to gain a little familiarity with that software. With that this walkthrough is getting rather lengthy and we've reached an excellent breakoff point at the end of the first half of this puzzle, so come back in a week for the conclusion giving you plenty of time to research the technology.