Enter the Cipher
Okay so I left off last week with a broken image, a cryptic note, and some homework, lets see how we get on and solve this one. The first thing to do is we haven't looked at that image yet, it says its corrupted but you could name it anything, it could just as easily be another file hidden in an image, but load it up and sure enough it fails. If you pop up the properties nothing really looks amiss there either, so maybe it is what they say it is? Let me let you into a little secret, a file extension (.jpg) these days is a little bit redundant, it helps systems figure out where they belong, but we saw a couple of weeks ago how magic numbers do that too. So lets do that with this one and see what we get.
~> xxd data/Corrupted.jpg | head 00000000: 03d9 a29a 67fb 4bb5 0000 0400 0210 0000 ....g.K......... 00000010: 0031 c1f2 e6bf 7143 50be 5805 216a fc5a .1....qCP.X.!j.Z 00000020: ff03 0400 0000 0100 0000 0420 0000 00c9 ........... .... 00000030: 1b58 5e9f b8f8 a416 696c 6c77 2303 e770 .X^.....illw#..p 00000040: 85c1 0122 a806 9b80 6396 a5e8 b5fd 2307 ..."....c.....#. 00000050: 1000 0000 7cc4 6cde 557c a4ec 23ce 4cbf ....|.l.U|..#.L. 00000060: 2506 9c95 0b8b 0000 0000 0142 0500 0000 %..........B.... 00000070: 2455 5549 4410 0000 00ef 636d df8c 2944 $UUID.....cm..)D 00000080: 4b91 f7a9 a403 e30a 0c05 0100 0000 4908 K.............I. 00000090: 0000 002a 0000 0000 0000 0005 0100 0000 ...*............
Oh well isn't that interesting, 03 d9 a2 9a but checking our database all the jpgs start FF D8 FF, it's almost like this was never intended to be an image at all. A quick search of the database and this one doesn't come up at all, it must be something obscure because the list couldn't possibly contain every file signature for every piece of software ever written. Think back to the note they left "This broken image is not what it appears, it is the database you have been looking for", what if this 'image' file really is just a database file and they changed the extension to throw people off the scent? Only one way to find out.
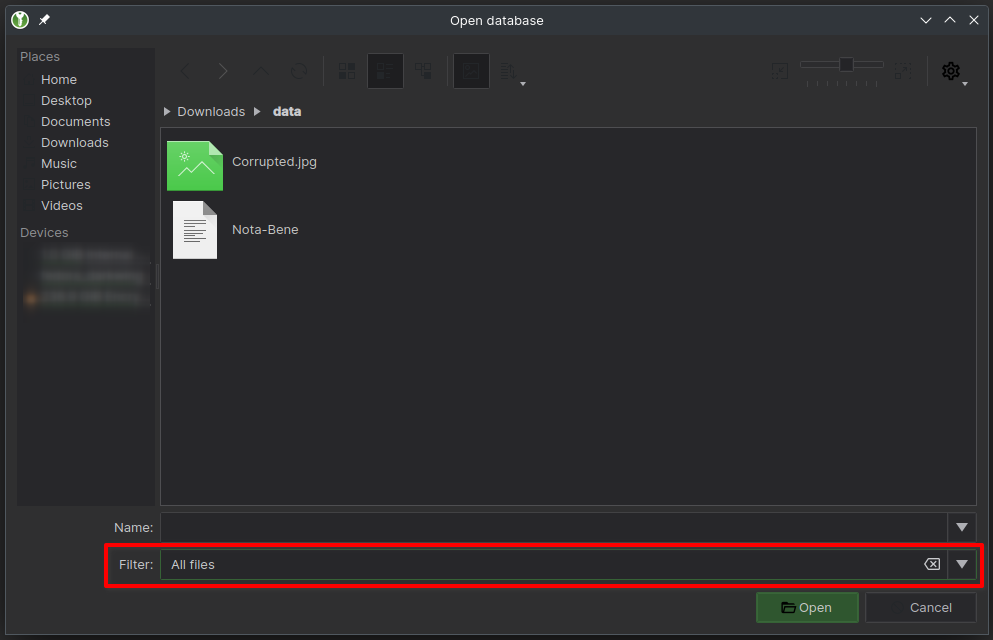
Loading up a random file in Keepass (I use XC as I find it has better cross-platform support) is really easy, just make sure you widen the filter to "All Files" so you can see them, then just select the one you need and hit "Open". We won't know if it's actually a database file until we open it but to do that we've got to figure out the security, at their most basic Keepass databases are secured with just a password. If you think back to the start we were given two hashes, and while we successfully cracked both, we never found a use for that second one, so lets give that a try here, type Emperor! into the box and press "Unlock".
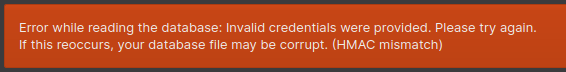
Hmm okay, that could mean three things, one, its corrupted, but lets ignore that one for now, two, the password was wrong which I can tell you it wasn't, or three, there's something more to this. This is where the power of observation and research really comes in look carefully at the login and you'll see there's the option to use a key file. You may recall the note said "Be sure to use this note as a key." pretty much any file can be used as a key file in Keepass, though I have to question why they would keep it with the database, but these folks haven't exactly been super secure so far.
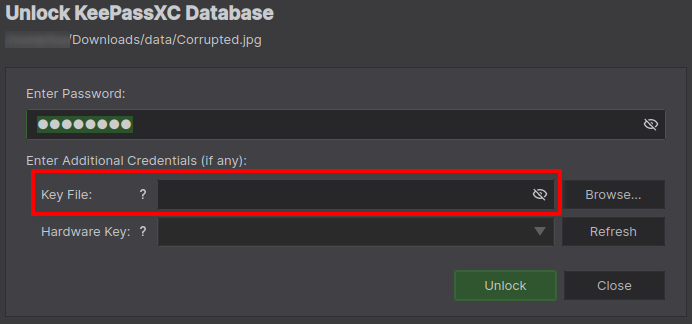
Add in the note as a key file, enter the password, hit unlock and would you look at that, the database opens, success! Now we have access to all their systems, or do we? Didn't that note also say "but we've modified it slightly for security"? Take a look and sure enough these passwords have been scrambled, but all is not lost, they've left us some notes to work with, all we have to do is figure out what they mean. The first thing we need to do is pick, Active Directory is at the top of the list but that'll be the domain admin password which gives you complete control over everything, so they won't have made it easy. Lets start with the one labelled "Encryption key", its probably the key to the encryption they've put on some device or other so perhaps an odd choice, but it's also conveniently in plain text, its basically a freebie for cracking the hash to get into the database so note it down and let's move on.
Next we'll tackle the Webserver, webservers host the company website so are often external to the company due to being public facing and one of the most common things to be broken into so this should be easy. There's no note but its clearly binary.
010000100110100101110100010100100110111101110100011110110110100001000101001100010010110101110100011000110011100101011111011001000101111101101111010011000011011001001010010101100101010001000100001101110100100101101010010010010101011000101101001100000111100000110000001100000011000000110000001100000011000000110000001100110010110101010111010001010101011101010000011110000100110001110100010100100010110101111000010011000100111101000111011010100111011101100111010110100100101001010110001100010011100001111101
So fire up CyberChef and lets decode it, all this one needs is "From Binary" stored under "Data format", copy in the binary string and it should give you the flag, nice and easy.
Onto Exchange, this is Microsoft's email server technology so usually a good place to check in to keep an eye on all the mail in and out of the company. As previously mentioned our team has gained access to this so it can't be too difficult, let's take a look. No note again but that looks familiar too, seems like we've got hexadecimal, just a more compact way of storing binary.
426974526f747b56355a79536356695635787774333838552d754474552d307830303030303030342d41307953583134615a447730594554422d6f7a61457d
Stick this in there too and use the "From Hex" method, sure enough we get the Exchange flag.
Alright lets take a look at Samba next, Samba is an old file sharing technology thats supported by most operating systems, as a result its quite prevalent but also tends to be full of security holes. This one seems a little trickier its a sequence of numbers, but not like binary or hexadecimal, so what do we do with this?
66 105 116 82 111 116 123 111 116 54 97 89 112 70 117 49 70 49 98 78 55 79 103 83 117 73 107 80 70 45 48 120 48 48 48 48 48 48 48 53 45 114 54 95 103 110 76 99 56 109 49 84 105 55 119 69 88 54 86 119 90 89 125
Well by now we're getting pretty familiar with different data formats and the way they store data, this is just another, answer me a question, how do you think a computer system that uses 1s and 0s for everything stores a sentence? Well as we've seen a single letter or character can be stored using something like ASCII the character "A" can be stored in binary as the pattern "100 0001" and as long as the computer is informed its ASCII it can look up in the table how to translate it, this known as the character's code, or charcode. So for a sentence you just need to figure out what code each letter including spaces and specials has and you can turn the whole thing into binary, because ASCII codes are always exactly 7 bits long so it always knows where they start and end. Of course all those digits can get a bit unwieldy so its not uncommon to write each code out in decimal so it can be better understood by humans. That's basically what we have here and again CyberChef has a method specifically for this known as "From Charcode" though it defaults to hexadecimal so you will need to edit the value to 10 to get your flag out.
VoIP is Voice over IP which is a fancy way of saying phones over the internet, in fact the term is quickly becoming redundant as the majority of phonecalls are handled this way now so in a roundabout way it's basically just the phone system. In terms of what the password is for, most likely if stored in a company database like this it is for the PBX which are usually virtual these days, simply put it'll be the login to the console that manages their phone system, this can actually be more powerful than you'd think as most businesses "record all calls for legal and training purposes" and the PBX is where that is done and usually also where they are stored at least in the short term.

A curious side-note as I used to do this for a job, most PBX systems as of the time of writing don't use any encryption on their calls as they pass across the network. I queried this with one of their engineers and was told "nobody does this because its considered too difficult to implement without affecting the calls", I've never tried to encrypt a phonecall, but this does jar with my knowledge of encryption, however at the time for corporate reasons I said nothing and carried on, after all maybe there's more to it than I'm aware of. Anyway as a result of this it means with a well placed Wireshark capture you can scoop up the phonecalls and if you know how you can literally just snoop in on that conversation. I know this because this was a method we would use to analyze problems and detect jitter in phonecalls. So as a result of this any company with a decent handle on security will ensure their PBX only talks to the handsets either directly on their internal infrastructure, or via a VPN to ensure nobody on an external network has access to their unencrypted phonecalls, though if you get onto their network, well there's very little they can actually do to stop you. Hopefully that doesn't scare you too much, CyberSec is full of horrifying realizations like these, anyway, back to the task at hand.
OvgEbg{_0R0sIafrrTkluSFac6Xtp-0k00000006-NtKCqJhJMC3WqYf5Kjh28}
This one doesn't look like any sort of data storage mechanism, and you'd be right it's quite literally been scrambled and that's the point, it uses a method of encryption to prevent someone without knowledge of the key from reading it. To call it encryption though is an overstatement, it'd be like calling an antique kiddie's trike a supercar, it just isn't, it's the same idea, but it could never measure up. What we have here is a cipher, and I'm going to teach you how you crack these, start by loading up CyberChef and find the method called "ROT13" under "Encryption/Encoding" and poof, there's your flag. Before we move on though lets understand what it did, it rotated the alphabet, this has another name the Caesar Cipher, where you take a number like 3 and you rotate the alphabet by that many letters so \(a \Rightarrow d\), \(m \Rightarrow p\), \(z \Rightarrow c\). ROT 13 shifts by 13 letters as the name suggests, why that specific number? There are 26 letters in the alphabet, so 13 letters is as far as you can go before you start coming back again. So if the ROT13 didn't immediately work, you could have altered its number to 0 and gone up 1 at a time and until you reached 26 to check all the different permutations of this type of cipher and that's not very many so you can easily see how weak this cipher is because it would take you no more than a couple of minutes.
Next up lets take a look at the NTP server, NTP is a protocol for managing time, no they haven't built a time machine, well not a useful one anyway. Basically NTP is how you manage time on your computers, they all have an internal clock of sorts but over time they drift, and NTP gives them a way to synchronize, why would a company need that? Well imagine a stock market company, they buy and sell millions of stocks every second of the day, and as a result those rates change even faster, so microsecond precision is important and all your machines need to agree what time it is at a given moment because a difference of a microsecond could mean millions of dollars. That said, most companies won't even have an NTP server, you don't really need one, all you need to do is make sure all your key machines query the same publicly available server, having your own is more about control of the time server and limiting how many public queries you make. This flag is fairly easy to decode, its simply base64 or MIME encoded, which is a way of storing data you often see used with databases as it can compact any file or data down into a string without losing anything. Just run the "From Base64" method under "Data Format" to retrieve the flag.
Qml0Um90e3JVdHlBaEpSRHBVM0ZmNXVKWllGd28tMHgwMDAwMDAwNy1pSTdqY0xtRFRtRkQyRmQ3WUM3SjR9

Okay its time to prep for some DNS poisoning, lets break the password to get into their DNS server! DNS is the system by which all the web addresses you remember work, without it the internet as you know it would just fall apart because everyone just implicitly trusts that when they put a name into their browser it pulls up the website that you requested. In fact not just humans rely on it, its how basically every piece of software your computer has even down to the operating system it uses pulls in its updates, its how you troubleshoot problems and even how you play games or watch TV, its how you know your internet is working. Just imagine if you can for a moment the chaos and the havoc someone could wreak if they could alter that system at will, and then remember that you probably don't even know the half of it, yeah, it's big.
AAAAB ABAAA BAABA BAAAA ABBAB BAABA AABAB AABBA AABAB ABBAA BABAB ABBAA ABAAA AAABA ABAAA AAAAB BABAB AAAAA ABBAA BABBB AAABB BAAAB ABABB BAAAB ABABA BAAAA AAAAB BAAAA ABBAA BBBBA ABBBA BAAAA AABAB BBABA ABBAA ABBBA ABBAB AAABA ABBAA AABBA AABAB
So in terms of this one it probably looks a bit like a song structure or something and its an odd one, but I have to admit when I made this one I made a mistake, I underestimated what it would do to the flag. Due to that I released an ammendment to the flag so that I could accept it in it's malformed state, and you'll see this reflected in the flags at the end. I've never seen this cipher not used in a humorous context, its an interesting approach but nonetheless trivial to crack, its known as the Bacon Cipher and works a lot like a binary encoding. I won't go into more detail than that as you'll rarely if ever see it, though feel free to read up on it if it interests you, the way to crack this one is simply with the "Bacon Cipher Decode" under "Encryption/Encoding". You may notice this is the first entry we've tackled that actually has a note I=J U=V A/B and that's because the default is to treat it like binary, the note simply specifies the settings you should use to undo the encoding, the important one being that you should switch to A/B.

So far you may notice I've not really covered how I know what each one is, and that's because these are all fairly recognisable just from a glance. Whether thats the telltale numbers with spaces of charcode, Caesar's habit of leaving none alphanumerics alone, MIME's distinctive appearance or Bacon's obvious coding system, given enough time you too will start to develop an affinity for seeing these encodings, though from here on it won't be quite so obvious.
I think this post is already long enough at this point, so tune in next week where we will tackle the second half of this database.