Taming the Shrew
Following on from the previous two posts and from here things start to get tough, though it still remains easy from the context of wider scale security. Its just we're now going to be tackling much harder ciphers which is very much an entry level topic, and more historical than they are practical, but there's a nice little surprise at the end for you. So far we've found and broken into the password database, done some data recon, forensics, cracked some hashes, and learned about some ciphers, we've taken control of the company webserver, their mail, phone and file systems, we can play with their DNS and NTP. Well, according to the scenario anyway as a real world scenario is more involved than this but hopefully you're learning some useful information, and developing the skills you will need if you ever want to do those things for real. Even the ciphers which are fairly trivial by modern standards we've either been given the key or been able to figure it out easily, but knowledge is the key to breaking them so I'll probably cover how to actually break them at some point in the future. For now lets get this task finished with.
Next up we're going to try and get the flags for DC1, DC2 and DC3, what does DC stand for? Data Center, why are there three of them? Redundancy. So in a modern organization all the services we have broken into so far would be run on Virtual Machines as its much more cost effective than having a separate server for each and much more secure and less problematic than just dumping it all on one server. These VMs as they're known are much like regular machines to interact with except there's no physical box, so what black magic is this? Well, its quite complex, but think of it like this, the VM exists within an actual computer, each one can have many and the computer lends its CPU, RAM etc to the VM to perform its tasks because it doesn't need 100% of them 100% of the time. So DC1, 2 and 3 are just physical computers rather than a datacenters themselves, DC1 will exist within one datacenter and DC2 in another, that way if DC1 one goes down, the VMs can simply be booted up on DC2 instead and remain available, and DC3 is a failover in case both DC1 and DC2 go down, usually DC1 and 2 will act together for diverse routing and loadbalancing but that's way beyond scope here. That's a laymans overview, but its also worth noting a truly modern company will be using containers in a similar manner instead as they are far more lightweight than VMs but the basic principle is much the same. Suffice to say the depth of those topics goes well beyond the basic knowledge I'm intending to impart here, and control of a host machine like these would afford control over any of the VMs or containers it runs.
CniQpi{Zn4rgYSpXyXt-eAmq0PPID-0s00000009-2K9gtmu0sJjlJJRSfyab0}
So DC1's note says simply a=87 b=19 which is pretty cryptic, though it is enough to solve this one you just need to figure out how. If you look at how it's structured though only the alphanumerics have been changed and case is preserved which implies whatever it is it's related to Caesar Cipher, the first step on seeing something like that would be run through the rotations, though you won't find anything. Take a look at the bit outside of brackets its pretty much guaranteed that should read BitRot given the others do and you'll notice no single shift will do that, and that's because this one is more complex. Since we know a lot about this cipher it narrows our search some what and it shouldn't take too long looking for a Caesar Cipher with a and b values before you come across the Affine Cipher. This one works very similarly to Caesar but where Caesar does \(y = x + a\) Affine instead does \(y = ax + b\) so if \(a = 3\) and \(b = 7\) instead of shifting by 3 \(B \Rightarrow E\) it is multipled by 3 then shifted by 7 \(B \Rightarrow D \Rightarrow K\) with \(A\) being index 0. Despite appearances this linear nature is no more secure than Caesar Ciphers as its still vulnerable to the same attacks. To undo this linear transformation CyberChef has the "Affine Cipher Decode" method, input the values \(a = 87\) \(b = 19\) and you should see the flag pop out.

iB_yD_PZe|oREbjB_f}xiRIfSjiQRsHJlo^X_G^nhV
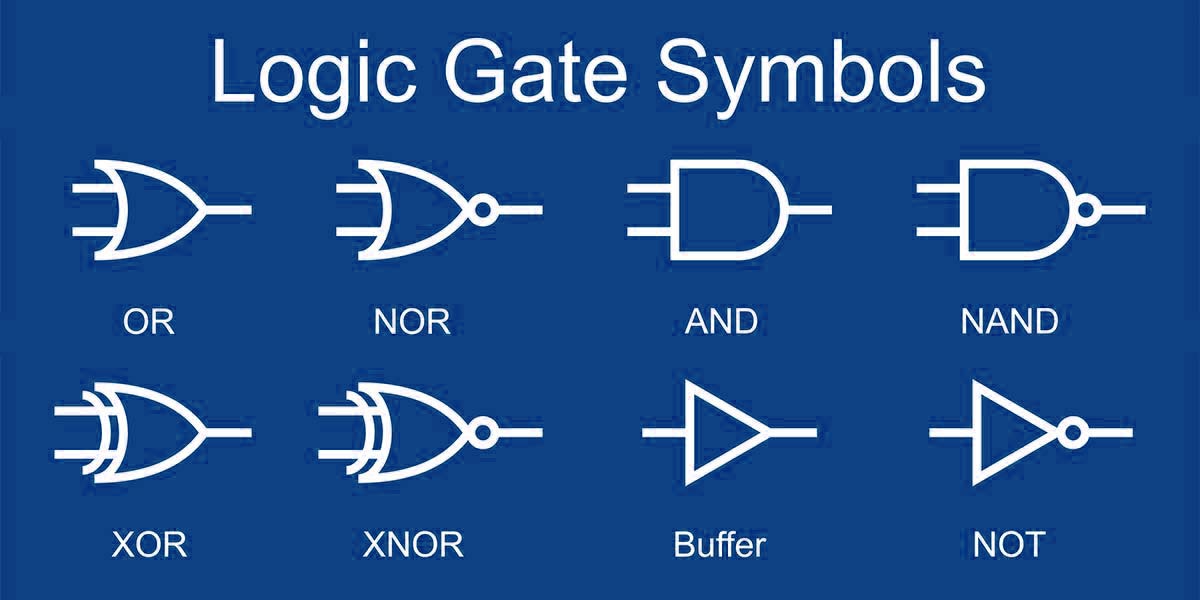
DC2 looks like a real headscratcher at first, but sometimes the most confusing thing is actually the biggest tell, having all those null characters implies something has probably been done to them on the binary level. Sure enough the note XOR key=43 confirms this. Clearly to prevent confusing their staff too much they just straight up gave them the name of the cipher, probably a good thing as it could have taken us many hours of playing around with binary transformations before we discovered it was an XOR cipher, remember the biggest enemy of security is usability, but they don't have to be on opposing sides. XOR is a logic gate, you might recall those is you ever learned about boolean algebra don't worry too much about all these complicated terms though its really simple. Imagine you have a simple statement such as "All elephants are pink." this statement can be true or false, that's what a boolean is, boolean algebra is a way of comparing two of these statements using the logic gates AND, OR and NOT.
The gates are just like they are used in speech, so "All elephants are pink and all pink things can play trombone" is two boolean statements bound by an AND gate if the first statement is true and the second is also true then the assertion that all elephants can play trombone is also true, otherwise it is false, OR is true when at least one of the two statements is true, and NOT applies the inverse of the one statement it is bound to. SO what of XOR? Well that is an exclusive OR, so it is true if only one of the statements is true, if both are true then it is also false, this isn't consider a basic logic gate as like NAND, NOR and many others it can be constructed from other gates. So if thats what it is why is it here? It turns out that XOR in particular has a really interesting property, you can encrypt data with it, and then most importantly with the correct key if you apply the same operation again it also decrypts the data for you, neat huh? This cipher isn't terribly secure though, well, not usually, the shorter the length of the key or if it is ever reused makes this cipher weak, but there are ways to make that a powerful tool that I won't go into here. How do we achieve this cipher? Simple, get your data in binary form, we've seen previously how to do that, and get your key that is usually just a number and put that in binary form too, now bit by bit compare each in turn using an XOR gate, this is actually trivially fast to do as CPUs are built from logic gates. The note rather neatly gives us the key, so input that using the XOR cipher and don't forget to tell it it's a decimal number and you should get the flag.
BjvUsy{YhUZ0noDHGI3_kcdZmJ8dr-0v0000000A-Ko3j0Ask5wczNR1-JC274}
And we're back to something like Caesar with DC3, though this one looks an awful lot less predictable than the others, no key given with the notes this time, just the word Trithemius whatever that means. If you put the word into CyberChef it won't bring anything up, and that plus the no key given is the reason this one above all the others gave people far and away the hardest time, but it is very possible and no further clues are needed it just takes a little research. Putting the name into Google should allow you to find this, though the explanation of it is a little tough to read, allow me to attempt to simplify it:
- Build a tabula recta by applying a Caesar Shift of -1 or 25 every row until you get back to where you started.
- Find the first letter of your message in the top row it should be the same as it started.
- Find the next letter in the top row then find the corresponding letter in the next row you haven't used, that is now your encrypted character.
- If you reach the bottom start back at the top again and keep going until your entire message is encrypted
Then to decrypt you repeat in reverse:
- Build a tabula recta by applying a Caesar Shift of -1 or 25 every row until you get back to where you started.
- Find the first letter of your message in the top row it should be the same as it started.
- Find the next letter in the next row you haven't used, starting at the top again if you've reached the bottom.
- Find the corresponding letter in the first row, that is your decrypted character.
- Repeat 3 and 4 until you've decrypted the entire message.
If it sounds slow that's because it is, all these old historical ciphers were done like this back before computers, thankfully now we know how it works we can do it programmatically by just approaching it slightly differently. If you've done some reading you may have learned that just like ROT13 is a specific case of a Caesar cipher the Trithemius cipher is just a special case of the Vigenère cipher. The Vigenère cipher is actually a bit easier to explain oddly enough despite being more advanced, you essentially apply a Caesar shift of exactly the amount of that letter of the key, so its like adding the plaintext to the key if you turn all the letters to their numerical values. An example will help, I'll use the message "potatoes" and the key "key":
\[ M = potatoes \\ K = key\]
\[ M_{i} + K_{i} = C_{i} mod 26 \\ M_{0} = p = 16, \; K_{0} = k = 11 \\ 15 + 10 = 25, \; C_{0} = 25 = z\]
\[ M_{1} = o = 14, \; K_{1} = e = 4 \\ 14 + 4 = 18, \; C_{1} = 18 = s\]
\[ M + K \Rightarrow C \\ potatoes + key \Rightarrow zsrkxmow\]
If you don't understand all the math don't worry, the last line is the most important, just understand that "p" Caesar shifted by 11 where \(Z \Rightarrow K\) is "z" and "o" Caesar shifted by 4 where \(Z \Rightarrow E\) is "s" etc. and that the key simply repeats to fit the message so keykeyke. So if you investigate it for a while you'll soon see that Trithemius is simply a Vigenère cipher where the key is ABCDEFGHIJKLMNOPQRSTUVWXYZ as the result is the same. Knowing that you can simply use the Vigenère Decode method and the lack of a key becomes obvious, congratulations you've just solved your first polyalphabetic cipher! Though the significance of that will probably be lost on you until you learn more about what that means.

Okay its now time to tackle the Firewall, but what exactly is a fire-wall? Well lets start with some devices you may have heard of routers and modems, most people I've met consider these names interchangeable but they are very different things. A modem is simply a device that negotiates a connection usually with an Internet Service Provider, think back to the old dial-up modems (if you're old enough to remember them) that would make a huge racket connecting to the internet, that's a modem. A router (pronounced route-err, a r-ow-ter is a tool for carving recesses from wood) is a device that allows communication across multiple layer 3 networks, so it spends all its time working with IPs and routing tables, its routers that make the Internet work, people think its black magic but really its routers connected to routers connected to more routers, and all that infrastructure requires special technologies and maintenance which is why its a miracle it works at all and network engineers like myself are usually not that surprised or interested when a website stops working. The confusion occurs because all most people have dealt with is their home internet box, in the past this was called a modem but now they call them routers, ultimately modem technology has been simplified and shrunk, so it is now easily contained within your home router that also handles the layer 3 networking modern internet connections have to be able to handle. Okay, thats all well and good but what about the firewall? A firewall is a router with access control lists, it exists to protect you from all the harmful traffic on the internet, and here's the rub, your home router also acts as a firewall, so modern networking can get very confusing unless you know what you're dealing with. The main thing is be grateful for your firewall, it is your first and last line of defence from all the malware you've heard about, though it can't protect you from everything.
AhsQns{Lvc3jVVW5hlbYYrWJ2uIkY-0r0000000P-0kwAE8C1igE5-pRhyOBPP}
Right so this one I made some sort of mistake, not sure if a cat walked across my keyboard or I accidentally added my testing code or what but ultimately if you follow the instructions as they are intended to be followed, the answer is wrong, here's the neat thing though, because of the simplicity of the cipher you can actually just figure it out from the information. That's exactly what people did when they encountered this problem so its actually ended up being even more of a learning experience than I intended it to be. Lets see what the note reads AutoKey primer=LDBISNMWHGP, if you were paying attention in the last one you may already know what AutoKey is, its again as you can tell from the ciphertext a polyalphabetic cipher, it works similar to the Vigenère cipher but rather than repeating the key which repetition is bad for security it extends the key using the plaintext out of sync with the message. Essentially lets take our message of "potatoes" and key of "key" again, so for the length of the key its the same so we know the first 3 letters are \(pot + key \Rightarrow zsr\) but then we include the message as the key so the next encoding becomes \(a + p \Rightarrow p\) then \(t + o \Rightarrow\), the key ultimately becomes "keypotatoes" and the ciphertext you receive is zsrphhel. Why would you do this? Well as I say repetition is bad for security, it generates a pattern and patterns are easy to detect allowing you to figure out and decrypt the problem, so the AutoKey cipher adds more randomness to the mix making it harder to interpret, so this cipher is considered more advanced than Vigenère, however it does also end up encoding most of the message twice which adds in an extra vulnerability that is actually how we can overcome my mistake in a moment.
Now CyberChef doesn't actually have a method for AutoKey or AutoClave as it is sometimes called, oh no! Don't worry, the dependency on a singular tool like that is actually something I warned about a few posts back with Hamming Codes so its important to remember they have limitations and don't include every form of encryption or cipher, not to mention you could effectively reuse the Vigenère cipher but having to type in the message yourself as a key is more hassle than its worth. If you Google for "AutoKey cipher" you should come up with a few sites that will do it for you DCODE is really good I use them a lot or there's Crypto Corner who have made a nice tool for this. So it should be a simple case of put in the ciphertext and the primer as the key and hit decrypt right? Well it would be if I'd done my job right but you should be starting to develop the skills now to recognise what you get out is still gibberish, and that's because the key is wrong. We can rectify this though the first thing you should get in my flags as you should be familiar by now is my name BitRot and the key applies first so lets try out some letters to see if we can generate that, as you input them you should also start to notice how you can move the letter forward or backward just by adjusting your key in the same way, after that it won't be long until you find the first letter is "z". Shortly after you should notice the others are too and are able to generate the intended start with "zzzzzz", the second thing you should notice about my flags is the central bit is a hexadecimal number in the form 0x00000000 and the observant among you will notice they're sequential so this one should be 0x0000000C, recognising the patter just keep adding "z" until you get the desired result as what you are doing is trying to correctly align the message to the right offset. After some trial and error you will find the key is "zzzzzzzzzzz" exactly as long as the primer, and you will have your flag, congratulations on fixing my mistake and cracking your first cipher, you'd be surprised how big of an achievement that is, you should be proud, ciphers may be considered fundamentally broken from an encryption standpoint, but one of this level often still requires significant amounts of computing hardware, data and time to break them, you just eyeballed this one with a bit of help.

Now we're onto the stuff so tough its legendary, lets go for the Proxy, I've seen experienced and talented engineers alike tearing their hair out trying to pivot through proxies so they're not easy, thankfully for you though you just need to decrypt the password. A Proxy gets its name from the legal construct where somebody stands in and does something on your behalf and the server does much the same, if you ever tried to look up some kind of naughty sites at school you probably encountered a proxy, it looks things up for you, but it can also refuse to do so if the blacklist disagrees with the content, and if you can only access that thing via a proxy it will ultimately prevent you from reaching it. A proxy is ultimately a network device and any type of network connection can be proxied, it can be used to bypass security restrictions, to concentrate traffic, the protect its users from malware or probing, or enforce restrictions and policies, there are a few kinds of proxy that are fairly common, but the most common is a web proxy that restricts web traffic based on policies set by the organization that set up the network.
MYDSYZ{O-TKIHLSR6UI1BEI2BKAGA-0Y0000000O-_VKRMSV1GAEPKFM4H3A1I}
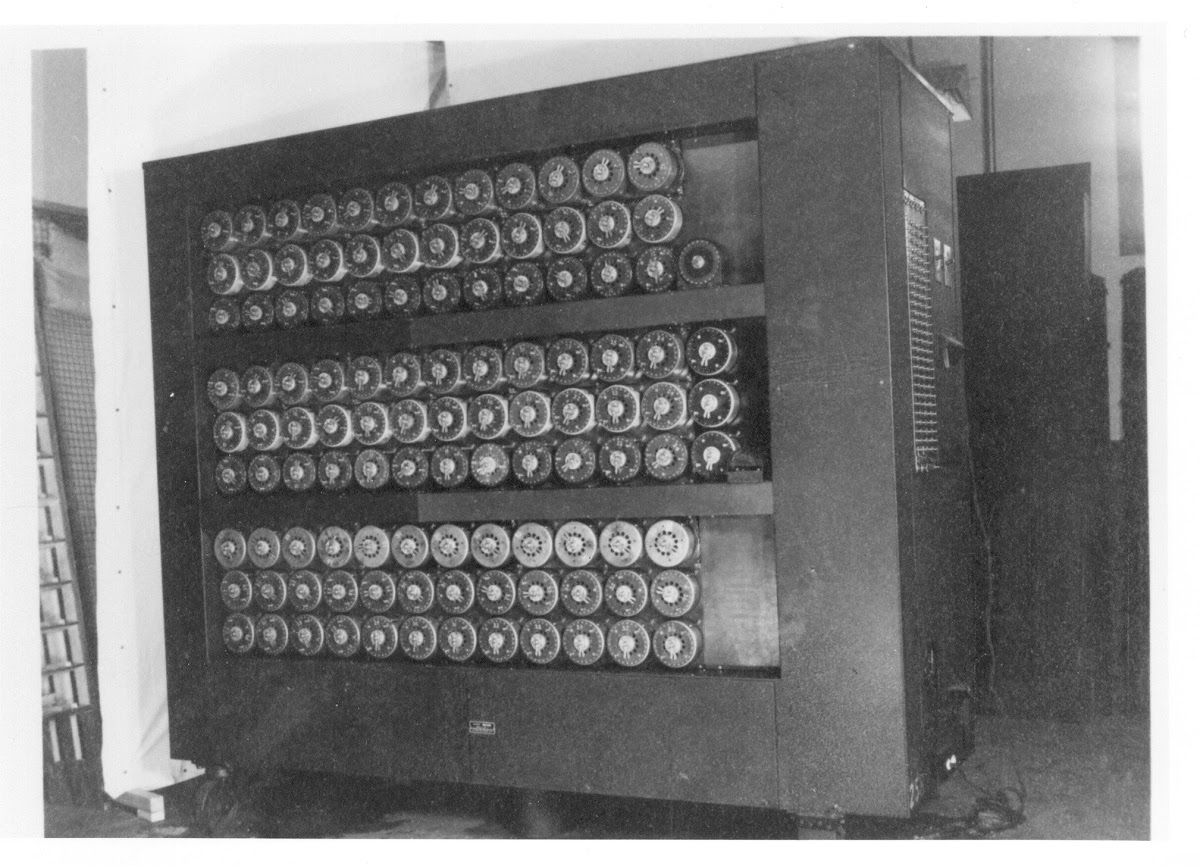
So this ciphertext looks distinctly different to the others, most notably its all capitalized, this is actually quite normal though, most ciphers don't distinguish between upper and lower case as case preservation can actually give away vital information, as a result your flags may be in a different case to the actual flag but its not worth worrying about so long as it's the right letter. The note this time is a lengthy one Enigma II r=W i=K, V r=X i=P, IV r=J i=T, Reflector=AY BR CU DH EQ FS GL IP JX KN MO TZ VW Plugboard=CF GZ OQ WV JY TL NE UI PB DA XM KS, that first word "Enigma" you may recognise, its a very famous system from WWII used by the Nazis to encrypt the communications of their High Command (pictured above), and you'd be right in guessing that's what this one is encrypted with. The rest of it looks very complex and that's because it is but we just need to understand more about how these devices work, CyberChef has a method for Enigma machines so pull it up as it will help with sorting through all the pieces.
The first thing to know about Enigma machines is that they come with a rotor system, and there are two types the standard 3-rotor system or the naval 4-rotor system as the man in charge felt the 3-rotor system was insecure so had some alterations made, the first section II r=W i=K, V r=X i=P, IV r=J i=T refers to the rotors here, it's done a little cryptically but you can see the 3 sets of numerals split by commas telling us this is a standard 3-rotor. These rotors were swappable with 8 different pre-programmed rotors that could be used in each slot, this is what the first bit of each refers to, its the roman numeral value assigned to each rotor type, so they are using a 2-5-4 rotor combination, the r is most likely the ring value, and the i the initial value as there are many different ways these rotors could be inserted and configured. After the rotors came the reflector that performed an additional translation but also meant no letter could encrypt to itself which it turned out was an exploitable flaw, the reflector depended on what sort of model you had but with the information given we can see this is a regular model 'B', just check the letter pairings to confirm for yourself. The final section refers to a plugboard, this looked a lot like the old telephone exchange switchboards and you'd use it in a similar way plugging a wire into two letter ports to join and swap them, this piece was actually the most brilliant part of the design as it allowed an extra layer of human randomness to help scramble the already encrypted signal, it looks like we've been given a series of letters to swap, so put all that in correctly, make sure its set to decode and you should be able to get the flag. You may have to remove the space it adds, and re-add the symbols but it should correctly output the letters for you. This system is no doubt immensely baffling even though you've just learned how it works, and you're probably wondering how you would even start to crack it without the key, the answer is its not easy, I'll maybe make that the subject of a future post. The fact that we managed to successfully break it in the 1940s is nothing short of a miracle and largely thanks to a lot of incompetence, masses of data, an army of human calculators working in secret, a large team of some of the world's most brilliant mathematical minds and no small amount of luck. My personal opinion is while Turing does rightfully get a lot of credit, any one of those minds at any other point in history would've been heralded as the greatest of their age, but I digress.
Looks like its time to crack the Active Directory password. Active Directory is a Microsoft tool for managing the domains, users, groups, roles and permissions of an organization, usually paired with [Group Policy] which can enforce the organizations mandates down to any machine attached to it's domain. Due to the ability to adjust the permissions on any domain-connected machine, access to AD is often considered to be the keys to the kingdom, it is usually limited to the Domain Admin account for this reason as both sit in a position of absolute power. Once a malicious actor has access to either of these two things it's basically game over, as this is a realm of God-like power with no higher power to remove it from them, much like the root account on a Linux system.
ZVDTDK{GHWQ02DDW5Y4RQTPBFGTBU-0H0000000J-U2IRCATX-DI0PBBLMWOCQ}
So this one looks pretty similar to the last one, even down to the note Typex 5 r=B i=C rev=true, 1 r=O i=W rev=false, 2 r=S i=U rev=true, 8 r=T i=A rev=true, 4 r=P i=Y rev=true, Reflector=AN BC FG IE KD LU MH OR TS VZ WQ XJ YP Plugboard=ZGHCKYJMDIWLPXNBTURSEFOQAV but something is a little off, and what exactly is a "Typex"? Well, when the Brits learned the Germans were using commercially available Enigma devices to encrypt their communications, they did what anyone would do, they went and got some of their own to test and play with, and when they began to see how it could be broken and that they could actually read German transmissions, they set about building a system that fixed all the flaws in the Enigma system, because what's better than reading all your enemy's messages? Rendering your own unreadable of course, that system was Typex, so you can think of Typex as a sort of Enigma 2.0 if you will.
"Typex" lets you know the encryption type and then it looks like its split into 5 sections which describe each of the 5 rotors the Typex system has. The first value for each is akin to the old numeral system and defines which of the 8 rotors has been chosen, "r" again refers to the ring value and "i" to the initial value, but the last one is new "rev" refers to whether the rotor has been reversed and carries a boolean value. The final two sections are similar to before refering to the reflector and plugboard for final switching of the letters. This system wasn't infallible but at the time proved uncrackable which was the aim, obviously the advancement of encryption algorithms continued but the Typex itself proved its worth and some were still being used right into the 70s. As with Enigma CyberChef conveniently has an encoder/decoder for this so just put in all the variables as the note specifies and you should be able to pull out flag, thus proving that as amazing as it is encryption is only as good as its weakest link and this company seems to have completely missed the importance of not just writing down all your secrets where anyone can find them. It's worth noting by the way you don't need the keyboard emulator it'll just make a mess of the whole thing so leave it set to "None".

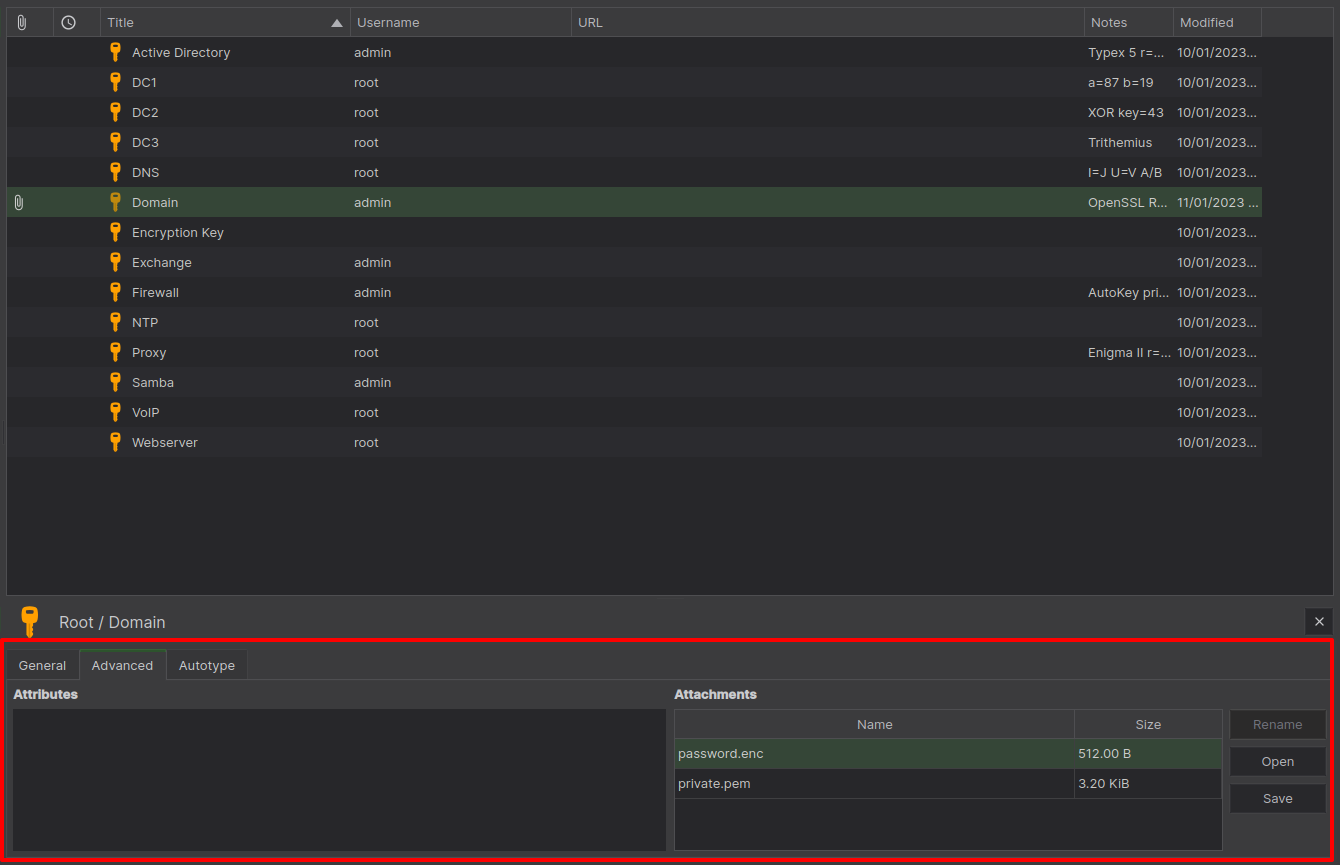
So, now what? Time to go after the top dog, Domain Admin, but what could possibly be harder to break than Typex? How about an actual encryption algorithm? See I've led you all this way, through technical knowledge and historical ciphers for a purpose, to test your mettle, and expose you to encryption as a whole, to show it isn't half as scary as people often think, but our journey isn't quite done. To finish this quest we have to cross the boundary from historical into current, to see how these clever ideas became something robust, insurmountable, and secure, and just as the last ciphers died out in the 70s that is when true cryptosystems began to be born. If this terrifies you never fear, just as with the ciphers the intent is not to make you crack it, but to show you how it works even the best cryptosystems are vulnerable to incompetent humans, and making leverage of that is an important skill, learning to actually crack these things is not an entry-level task, but it is something I can teach in time. First though, try copying out the ciphertext as before for this one and you'll notice nothing is there, how odd, lets read the note OpenSSL RSA, see attached. To those who researched Keepass you may know, you can actually attach files to your entries and that's what it's talking about, so go find those, you should be able to see them under the "Advanced" tab, they're downloadable.
A little about RSA, you can read all about Ron Rivest, Adi Shamir, and Leonard Adleman and how they came up with the system as a solution to the world's privacy problem on Wikipedia, so I won't go into that. Nor will I cover in great detail Public/Private Key Cryptography or the differences between Symmetric and Asymmetric encryption or the Diffie-Hellman exchange, all of these already have countless guides on them that go into excellent detail for you. Instead I will only cover what is relevant to the topics I'm describing and that is RSA itself, but for now I will only introduce it in a simplified way, as I will cover it in much greater detail when I introduce you to my corrupted RSA programs designed to teach you how to spot flaws in cryptosystems in some other blog post.
Imagine Alice wants to talk to Bob, if she's in the same room that's easy, and if she wants to stop Chad overhearing she can simply whisper, but now imagine Alice lives in New York but Bob lives in Tokyo, it's easy enough to use something like an email to talk to Bob thanks to the Internet. When Chad starts trying to listen in though it becomes a lot harder, and Alice doesn't know how to implement any of the fancy tools to protect email so she instead knowing some maths decides to invent one. She wants to encrypt her email in a way that it can only be read by Bob so she has Bob come up with two large prime numbers that he notes down, multiply them and send the result to her, of course Chad is listening and also gets access to the result. Alice then encrypts her next message using this result in such a way that you can only decrypt it by knowing the two primes, Alice then sends this message to Bob. Bob can decrypt the message easily enough and reads the message no problem, Chad has both the encrypted message, and the key used to make it, but without the primes used to make the key he can't decrypt the message. Theoretically Chad could try to guess the prime factors used to make the key but this is a computationally hard problem, at least until sufficiently powerful quantum computers arrive, if the primes used are small its possible but Alice explicitly asked for large primes, so it could take Chad millions of years even if he had Google's datacenter at his disposal.
This is effectively how RSA works though it has been simplified somewhat for ease of understanding, the combined key is known as a public key because it can be shared publicly, and the two primes are known as a private key because you keep them private. As promised we're about to break this encryption by exploiting a weakness, usually public keys are known as certificates and tend to have the extension .crt, whereas private keys tend to use the extension .pem, this isn't either universally true or foolproof but as a general rule that's how it tends to be done. Our weakness is people, notice how in the database is stored two files, firstly "password.enc" the encrypted password file, and "private.pem" which looks suspiciously like a private key, and the note told us the program we need is OpenSSL, now all we need to do is google the commands, it shouldn't take you long to find that you need something like this.
~> openssl pkeyutl -decrypt -inkey private.pem -in password.enc -out password.txt
If it runs correctly there will be no output, a simple cat password.txt should read the file you just made and give you the flag. Congratulations you've just cracked RSA via pure human stupidity, and slain the dragon at th end of this dungeon. Thank you for reading this blog and taking part in my challenge, if you're looking for something more to do TryHackMe should have their Advent of Cyber out by now, its a seasonal event designed to teach newbies basic hacking skills, it's good fun I'd recommend it! Here are the promised flags for checking against, hopefully you did well, and don't mind any differences in case, sometimes the ciphers can garble them a little.
Flags
BitRot{CgvyFyAnH1wMkd24NhZYY5-0x00000001-Hu7DFN_54FP-v3Jxooa90} - Obscurity (Steganography)BitRot{NBMa7RLiwsSdkb1b67hWz5-0x00000002-UinCGG2zefPzKtRdSRP2a} - Obscurity (Hash) - Encryption Key
BitRot{hE1-tc9_d_oL6JVTD7IjIV-0x00000003-WEWPxLtR-xLOGjwgZJV18} - Obscurity (Binary) - Webserver
BitRot{V5ZyScViV5xwt388U-uDtU-0x00000004-A0ySX14aZDw0YETB-ozaE} - Obscurity (Hexadecimal) - Exchange
BitRot{ot6aYpFu1F1bN7OgSuIkPF-0x00000005-r6_gnLc8m1Ti7wEX6VwZY} - Obscurity (Character Code) - Samba
BitRot{_0E0fVnseeGxyhFSnp6Kgc-0x00000006-AgXPdWuWZP3JdLs5Xwu28} - Obscurity (ROT13/Caesar Cipher) - VoIP
BitRot{rUtyAhJRDpU3Ff5uJZYFwo-0x00000007-iI7jcLmDTmFD2Fd7YC7J4} - Obscurity (Base64/MIME) - NTP
BitRot{fgfn2x5nJcJbx_An-zdsMs-0x00000008-ND53HU25wBPUdvJ7Vbs5k} - Obscurity (Bacon Cipher) - DNS
Alternate accepted: BITROTFGFNXNICIBXANZDSMSLRBRN?PRF?NPOCNGF
BitRot{Si4unPXoMpMa-hVfr0OOTE-0x00000009-2Z9nafd0xWwcWWUXkpvy0} - Obscurity (Affine Cipher) - DC1
BitRot{q9NWDy-n2IAitM8VSBybM3-0x0000000A-B6zTyXca2GD9ustlu9EC8} - Obscurity (XOR Cipher) - DC2
BitRot{SaMQ0ddRUST3_ullGsO8hu-0x0000000B-Kn3h0Xof5qvrEH1-YQ274} - Obscurity (Trithemius/Vigenère Cipher) - DC3
BitRot{Mwd3kWUO5ounFMvTZ2yOwK-0x0000000C-0fkFL8D1ksI5-fUftEWEM} - Obscurity (Autokey Cipher) - Firewall
BitRot{j-yloOQrq6Ce1VKx2wSPLB-0x0000000D-_RehIkS1KuNfjtH4g3m1s} - Obscurity (Enigma Cipher) - Proxy
BitRot{JMXZ02YaQ5k4BAfwFRTEic-0x0000000E-E2eSdLmG-yP0Wmyhkkcyw} - Obscurity (Typex Cipher) - Active Directory
BitRot{l8HvzPeF4fo8AXjqNkJBDj-0x0000000F-Tiu6XshSQa88N-nncERHI} - Obscurity (RSA Encryption) - Domain